With the opening of the Consumer Electronics Show in Las Vegas, the IoT has moved beyond the initial hype phase and even past the phase of early deployments into what I call the “parental awareness phase”. That is to say, my parents, both of whom first setup a Facebook account just a few months ago, have now heard of the IoT. This morning my mom asked me if I was going to the show in Vegas to learn about the “new IOT electronics”.
However, if my mom were to ask an employee at BestBuy, “Is this new Internet of Things thermostat, garage door opener, or smart door lock, secure”, I don’t think she would get an accurate answer today.
In July of 2014, HP Labs did a study of 10 popular IoT devices and found that the security was shockingly bad. The researchers studied 10 devices, looking at the end-to-end security capabilities of these devices including privacy protection, authorization, encryption, user interface protection, and code security.
They found that 70% of the devices had at least one MAJOR vulnerability! By the time they completed their study, the researchers identified over 250 vulnerabilities, an average of 25 security vulnerabilities per device. Security was clearly an afterthought – or worse – for these devices.
An average consumer, or even a security savvy consumer, has little ability to know which brand of IoT device has better security or even any security. An OEM may claim “built-in security”, but that phrase alone means little.
The Role of Security Standards
IoT standards groups are emerging to address issues of interoperability, communication protocols and, yes, security.
At the end of the day, if security standards for IoT devices are to be useful, they must help the average consumer evaluate the security of an IoT device. As these standards are being developed, they should maintain focus on this end goal.
Achieving this will undoubtedly take time, but it is, in my mind, the only true measure of success. IoT security standards must aim to serve as the cyber equivalent of an Underwriters Laboratories (UL) or CE safety ratings.
Standards groups should strive to create an IoT Security Standard (ISS) that is measurable and defines a minimum standard of security for devices. Consumers can trust that devices that are ISS rated provide a reasonable or acceptable level of security for common use.
This security rating could one day be used by the insurance industry in evaluating cyber-insurance claims and big-box retailers could choose to only sell ISS rated products. Most importantly of all, consumers such as my parents would have some way to evaluate the security of products they purchase.
The electrical power infrastructure and industrial automation markets are already moving in this direction with the and IEC security standards that apply to their respective markets. NERC-CIP defines a set of security requirements for equipment operating within the North American power grid. IEC-62443 is a security standard for industrial automation and control systems. Each of these creates a baseline that device OEMs must meet when developing their products. If a device meets these security requirements the user can be assured that the device meets this baseline for security.
Creating a Security Standard
Cyber security is a difficult challenge and it would be naïve to think that we will see a security standard that will eliminate all risks of cyber-attacks against IoT devices anytime soon. Even so, a security standard can ensure that devices meet reasonable standards for security. There are a number of fundamental security capabilities that should be included in any IoT device.
We have defined a framework for IoT device security that provides a number of essential security features.
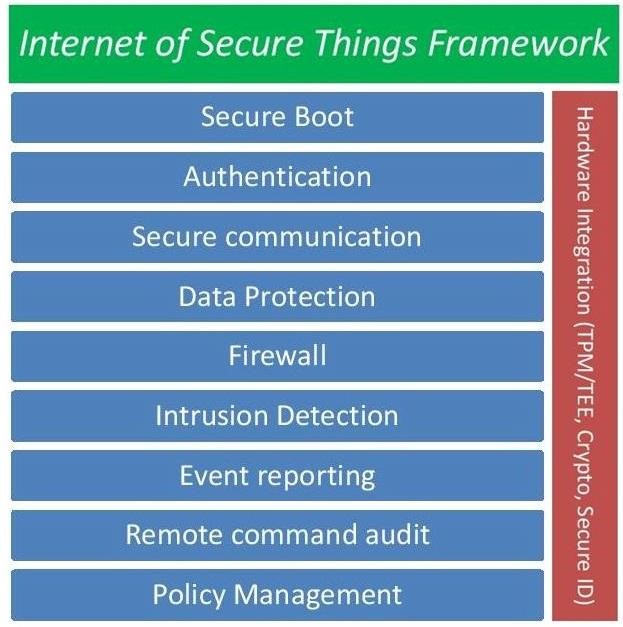
A security framework provides a foundation for evaluating and verifying the security capabilities of IoT devices.
There are many elements that must be addressed in any IoT security standard. Hackers thrive by discovering the weak link in a security implementation. Systems or standards that fail to provide complete, end-to-end security are bound to fail.
A successful security standard will provide:
- Protection for the device: by ensuring only authentic code from a trusted source is allowed to run on the device.
- Protection for data: by providing secure communication, data-at-rest protection and secure decommissioning of devices.
- Awareness of attacks: by including security monitoring, intrusion detection and integration with security management systems.
- Security management: enabling updates to security policies in response to emerging threats.
- Machine to machine authentication: ensuring that IoT devices are only communicating with other known, trusted entities.
Challenges for IoT Security Standards
In addition to the normal challenges of creating standards, an IoT security standard must address the challenge of scalability. IoT devices range from very small, very cost sensitive sensors using mesh networking technologies to sophisticated gateway devices and sophisticated endpoint devices such as cars, industrial automation controllers and weather satellites. The security requirements, potential attack vectors and computing resources available for security vary widely between these devices.
While this is a challenge, it must not become an excuse to ignore certain classes of devices or to fail to develop a standard. The embedded computing industry has developed sophisticated hardware and software systems that scale to meet the computing and price challenges of this vast range of devices. I have no doubt the industry is also capable of developing security standards, and the corresponding implementations, that scale to meet these diverse requirements.

“IoT Security Standards need to provide broad protection from cyber-attacks”
Getting started
As shown by the HP Labs research study of IoT device security, we clearly have a long way to go, and we must get started today. Just because there are no standards in place, companies building IoT devices must not wait to start implementing security. Solutions exist today to help OEMs build security into their devices and if they begin building security into their devices today, they will have a head start as security standards are defined.
Better yet, companies can be proactive and help define the standards. This will allow them to align product development efforts with emerging standards, ensuring compliance as standards are released. Getting started today on adding security only benefits both the companies building the products and the consumers that use them.
Emerging standards for IoT security
As an emerging market, Security standards are still evolving for IoT devices. Many of the existing security standards are focused on a specific industry or sector. NERC-CIP security standards , for example, were developed specifically for the electric utility industry. A similar, but more encompassing security standard is the NIST Cybersecurity Framework which is applicable to financial, energy, healthcare and other critical systems, and is designed to help these industries better protect their information and physical assets from cyber-attack. In the medical arena, the U.S. Food and Drug Administration has provided recommendations to manufacturers for managing cybersecurity risks to better protect patient health and information.
In addition to these industry specific security standards, a number of new standards specifically for IoT services are beginning to emerge. These standards are beginning to address a wide range of security concerns including security protocols for communication between IoT devices, threat modeling, device protection requirements, security architectures, secure software development processes and security robustness testing.
In addition, a number of IEEE standards address security elements that are applicable to the Internet of Things. These include: IEEE P1363 a standard for Public-Key cryptography, IEEE P1619 which addresses encryption of data on fixed and removable storage devices, IEEE P2600 , a standard that addresses security of printers, copiers and similar devices, and IEEE 802.1AE and IEEE 802.1X which address Media Access Control (MAC) security.
Summary
The IoT has entered a phase of mass usage and it will nolonger be acceptable that 70% of IoT devices have a major security vulnerability. It will take time for security standards to reach a level where customers can feel confident in the security of a device based on a security rating, but we must start moving in that direction.
While security standards are being developed, OEMS can begin building security into their devices to get started in creating the Internet of Secure Things.
- Source: Mathew Sparks, The Telegraph.co.uk. Average Internet of Things device has 25 security flaws. http://www.telegraph.co.uk/technology/internet-security/11000013/Average-Internet-of-Things-device-has-25-security-flaws.html
- Source: HP Intenet of Things Research Study. http://fortifyprotect.com/HP_IoT_Research_Study.pdf

Alan Grau
President and co-founder of Icon Labs
alan.grau@iconlabs.com
Alan Grau is President and co-founder of Icon Labs, a leading provider of security software for IoT and embedded devices. He is the architect of Icon Labs’ award winning Floodgate Firewall. Icon Labs was named a 2014 Gartner “Cool Vendor” and 2015 Gartner “Select Vendor”, and is focused on creating The Internet of Secure Things by providing a security from for even the smallest IoT devices.
Alan has 25 years’ experience in telecommunications and embedded software marketplace. On December 29, 1992 Alan co-founded Icon Labs, an embedded systems software development company whose clients include Motorola, Lucent Technologies, Intel and Tellabs. Prior to founding Icon Labs he worked for AT&T Bell Labs and Motorola. Alan has an MS in computer science from Northwestern University.