The Evolving Internet of Things (IoT) Requires New Approaches by Colleges and Universities in Educating All Students in Cyber Security
Abstract
The Internet of Things (IoT) is quickly evolving with 2016 predicted to be a critical year for the growth of connected devices, the sheer volume of data captured, and the types of ‘things’ connected (human-to-machine, machine-to-machine). The machine-to-machine category is growing at an exponential rate along with the data captured and communicated to databases for categorization and analysis. Colleges and universities are challenged to educate students across curriculum to understand the underlying technologies and the application of this technology to solve everyday problems. Students must learn that the IoT surrounds them and is already a critical aspect of their daily lives. Business, engineering, computer science, and cyber security departments across the country must plan to address student awareness through revamped departmental curricula and interdisciplinary opportunities across departments. It is this generation of future workers who will be tasked to solve the issue of security within the IoT. This article does not advocate a new degree, but, rather, a comprehensive interdisciplinary systems approach.
Introduction
In January 2016, a panel of experts discussed IoT security and privacy issues at the Consumer Electronics Show (CES) in Las Vegas, NV and drew attention to the rapid spread of devices connected to the net. The panel cited the following facts:
- There are 25 billion connected devices;
- There are more devices than humans on earth;
- Devices exchange data without human intervention and can be remotely activated;
90 percent of connected devices are sharing personal information with more than 70 percent of those devices sharing information on unencrypted networks (Mansell, 2015).
With that degree of proliferation, cyber criminals are viewing the spread of unprotected Internet-connected devices throughout the world as a welcome target in end-point device compromise. Compromising these Internet-connected devices is the first step in infiltrating the enterprise networks of major corporations and governments.
Business leaders, cyber security and network design professionals, as well as software and hardware vendors, face new challenges in protecting their network infrastructures and the Internet-connected devices. Colleges and universities must step up and address these new security challenges within their curricula to better prepare students for the security challenges they will face in the workplace. This paper discusses the Internet of Things (IoT) security challenge and some actions educators can take to begin to address this growing problem.
The IoT Defined
There are many definitions for the Internet of Things (IoT). The IEEE definition of the IoT is, “A network of items — each embedded with sensors — which are connected to the Internet” IEEE, 2015. The IoT has also been referred to as Cyber Physical Systems (CPS), M2M (machine to machine), and simply Industrial Internet and Connected devices. Figure 1 depicts the generic topology of the IoT viewed in layers to include the Datacenter, Gateway, IoT Devices and Sensors. Figure 1 also depicts that within the IoT architecture, data is acquired by smart devices, aggregated at the gateway and categorized and analyzed at datacenters in order to present the data as useful information to the consumer. Figure 1 also accounts for legacy devices (brown field) and new devices (green field), which when deployed on the same network present complex integration challenges to network and security operations.
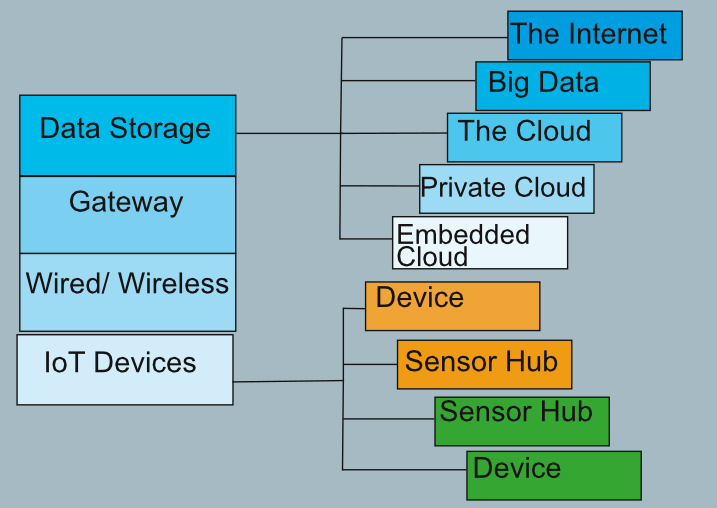
Figure 1: IoT Topology. Michael Strittmatter (2016). Based on diagram in Internet of Things Topology, Wind River (2015).
Internet-Connected Devices
As mentioned by the Cloud Security Alliance (CSA, 2015) the major stakeholders in the IoT ecosystem are banking and finance, public services, manufacturing, smart city, retail, health and energy. IEEE, 2015 also identified additional stakeholders such as consumers, regulators, and insurance companies. In the healthcare sector Internet-connected devices range from fitness watches to heart pacemakers. In the energy sector utilities have implemented smart meters connecting our homes to our utility company via a wireless Internet connection.
According to the World Semiconductor Trade Statistics, automobile safety systems are equipped with a swarm of 28 sensors (WSTS, 2013). These automobile sensors detect conditions such as tire air pressure, air bag pressure, and collision detection. These sensors also control the critical road-to-vehicle and vehicle-to-vehicle communications systems.
In the retail sector stores are using automated checkout, proximity advertising and smart vending machines. Smart cities have implemented smart meters, traffic management systems, and video surveillance for public safety. In the manufacturing sector factories are using robotics to assemble cars, and RFID sensors are used for inventory control and tracking the movement of goods (CSA, 2015).
While the list of stakeholders and industry examples are not all-inclusive, it does offer significant evidence of the need for cross-field training and awareness. Auto manufacturing provides a good example of multiple stakeholder involvement. Potential system vulnerabilities must be minimized in the R&D phase. Failure to do so ultimately affects the end users, which will then return to impact the business operation through events such as recalls and lawsuits. Awareness through training and education will help mitigate these issues.
The Threat Is Real
The threat to these Internet-connected devices is very real and continues to evolve quickly as public reliance on these devices increases. On September 10, 2015, the U.S. Federal Bureau of Investigation (FBI) issued Internet Crime Complaint Center (IC3) Alert # I-91015-PSA which alerted the public to the emerging threat to the IoT presented by cyber criminals (FBI, 2015). FBI Alert #I-91015-PSA not only defined IoT devices but also discussed the risks posed to these devices by cyber criminals.
FBI Alert #91015-PSA also discussed several reported incidents worth noting in this article. First, cyber criminals exploited gaps in a closed circuit TV system rendering this countermeasure useless to security officers. Second, criminals can exploit unsecured wireless connections for automated devices, such as security systems, garage doors, thermostats, and lighting. Third, cyber criminals can originate e-mail SPAM attacks from home-networking routers, connected multi-media centers, televisions, and appliances. Lastly, cyber criminals can exploit security weaknesses in monitoring systems embedded in our control networks in power generating and distribution systems (FBI, 2015).
In 2015, hackers exploited the vehicle control system of a Jeep Cherokee driven by Wired Magazine reporter Andy Greenberg by compromising these same communications systems while the reporter drove the vehicle down the highway in St. Louis (Grenoble, 2015). In February 2015, during a CBS 60 Minutes episode, Defense Advanced Research Projects Agency (DARPA) scientists demonstrated a similar compromise of automobile systems such as brakes and wiper systems of a vehicle driven by 60 Minutes reporter Leslie Stahl (CBS, 2015). In July 2015, these two much-publicized incidents may have prompted U.S. Sens. Edward Markey (D-Mass.) and Richard Blumenthal (D-Conn.) to introduce a bill forcing automobile makers to offer more protections (Grenoble, 2015).
The Challenge
The challenges in protecting Internet-connected devices such as those in automobiles from threats are many. Cyber security experts protect these Internet-connected devices by applying the three pillars of cyber security: confidentiality, integrity, and availability, also known as CIA. One issue with such IoT devices is the generally limited processing power, memory, storage, communications capabilities, and power built into the systems, all of which are required at a more enhanced level than exists to support the use of encryption, strong authentication mechanisms, and virtual private networks (VPN) (CISCO, 2015). Protecting these devices will require some new thinking from hardware and software vendors as well as current and future cyber security experts. In addition, there needs to be a focus on partnerships between future technical (e.g. engineers) and cyber security experts. The first step in this new partnership should be with educational institutions of higher education. Interdisciplinary communication on associated topics offers the potential of greater understanding to properly address these issues. Cooperation in solving these developmental issues will go a long way towards reducing the vulnerabilities, which currently exist in IoT devices and systems.
An additional challenge is protecting millions of legacy devices currently in use, which do not have the capability to implement the latest countermeasures. Similar to systems in automobiles, these devices fall short of the required technical capabilities that would allow the implementation of stronger encryption standards, or any encryption for that matter, and are limited by the devices processing power, power, memory, and storage and communications capability. These limitations also affect the device’s ability to support strong authentication. The use of VPN connectivity is a possible countermeasure which provides device-to-network confidentiality. Another threat lies in the chips at the center of IoT devices, which are globally sourced requiring the supply chain be assured against counterfeit chips and other inserted components (Leef, 2015).
From an enterprise network perspective, managing and protecting potentially millions of devices that are constantly connecting and disconnecting from the enterprise network is a huge challenge and concern. Such devices require logical and physical security integration. The physical security of a device can be easily compromised if cyber criminals gain physical access to that device and overcome whatever security measures happen to be implemented. New countermeasures such as kill switches (permanently disable the device), and remote wipe (remote erasure of contents of memory and storage) must be implemented to prevent compromise of collected data on the device, user credentials and more importantly the enterprise network via the compromised device.
Countermeasures
In addition to noting vulnerabilities in IoT devices, FBI Alert #91015-PSA also lists viable countermeasures which can be implemented to protect these Internet connected devices. These countermeasures are routinely applied to more capable network devices by cyber security professionals; however the physical limitations of IoT devices will limit the viable security options. We previously mentioned measures such as encryption, strong authentication and VPN’s exceed the ability of the IoT device to implement security measures due to limited memory, power, storage and CPU power. With that said the FBI offers some very basic common sense measures that are often overlooked and not implemented. For example consumers should purchase devices for the intended purpose, change the default passwords, and update the software when patches become available.
IoT device security must be evaluated under a risk management framework so that threats and vulnerabilities can be systematically identified and appropriate countermeasures devised and implemented by cyber security professionals. The application of a formal risk management process by the organization will help identify measures, which effectively address each vulnerability. While protecting IoT devices is far from business as usual for cyber security professionals, using a systematic approach to address the threat is the best course of action to achieve IoT-related security.
Conclusion
While the Internet of Things promises added convenience and efficiency, it also brings a new dimension of cyber and physical security issues. With the current rush to market mentality of device and network developers, future retroactive security solutions will be left to the next generation of security solution providers. Colleges and universities will be challenged to address IoT security via traditional departmental curricula and approaches. Solutions to the IoT security challenges are both multidimensional and interdisciplinary. Business and educational leaders must assure the supply chain of chips and other vital components, protect consumer privacy, and understand that their future success will be based on how well they harness the power of IoT technology to provide new sources of immense amounts of data about their customers and the business environment. Engineers and computer scientists must understand cloud computing and design IoT devices and supporting networks which can be protected utilizing best practices in secure coding, tamper resistant hardware and more secure networks utilizing strong encryption and authentication, and VPNs. Cyber security academics and other professionals are challenged to identify best security practices to be applied throughout IoT and supporting networks lifecycle (from concept to disposal) using an interdisciplinary systems approach. As Chris Rouiland, founder and CTO of Bastille, a provider of threat detection software for IoT devices recently noted, “Enterprises will start to find that compromises are entering their networks through things like wearables, m2m communications and industrial control systems” (All, 2016). While the IoT presents the promise of helping people, especially those with disabilities to lead more productive lives, the threats posed by IoT insecurity will emerge as the number one cyber challenge in the very near future. America’s higher education system must be prepared to provide the next generation multi-disciplined cyber security solution providers.
References
CBS (2015). CBS News 60 Minutes Program (video) 6 Feb 2015. Retrieved from http://www.cbsnews.com/news/car-hacked-on-60-minutes/
CISCO (2015). Securing the Internet of Things: A Proposed Framework. Retrieved from http://www.cisco.com/web/about/security/intelligence/iot_framework.html
Cloud Security Alliance (2015). Security Guidance for Early Adopters of the Internet of Things – April 2015, https://downloads.cloudsecurityalliance.org/whitepapers/Security_Guidance_for_Early_Adopters_of_the_Internet_of_Things.pdf
All, A. (2016). eSecurity Planet. Webcam Hack Shows IoT Security Threat. Retrieved from: http://www.esecurity planet.com/print/network-security/webcam hack. January 12, 2016.
Federal Bureau of Investigation (FBI) (2015). Internet Cyber Crime Center (IC3), Alert Number I-091015-PSA (September 10, 2015). Retrieved from http://www.ic3.gov/media/2015/150910.aspx
Grenoble, R. (2015). Hackers Hijacked A Jeep With A Reporter Inside, And 5 Other Scary Hacks. Retrieved from http://www.huffingtonpost.com/entry/hackers-hijacked-a-jeep-with-a-reporter-inside-and-5-other-scary-hacks_55ae9091e4b0a9b94852b44f
Institute of Electrical and Electronics Engineers (IEEE) (2015). Towards a definition of the Internet of Things. Retrieved from http://iot.ieee.org/images/files/pdf/IEEE_IoT_Towards_Definition_Internet_of_Things_Revision1_27MAY15.pdf
Leef, S. (2010). Internet of Things meets Hardware Cybersecurity. Retrieved from http://www.oregontechtalks.org/speakers/2015Files/SergeLeef.pdf
Mansell, W. (2015). Policy Makers Try To Define Security, Privacy With The IoT. Retrieved from http://www.idigitaltimes.com/policy-makers-try-define-security-privacy-iot-501712
Sorrell, S. (2015). Juniper Networks: The Internet of Things: Consumer, Industrial & Public Services 2015-2020, http://www.juniperresearch.com/researchstore/key-vertical-markets/internet-of-things/consumer-industrial-public-services
Wind River (2015). Security in the Internet of Things. Retrieved from http://www.windriver.com/whitepapers/security-in-the-internet-of-things/wr_security-in the-internet-of-things.pdf
World Semiconductor Trade Statistics (WSTS) (2013). The smart and connected vehicle and the Internet of Things San Diego CA. Retrieved from http://tf.nist.gov/seminars/WSTS/PDFs/1-0_Cisco_FBonomi_ConnectedVehicles.pdf
 Dr. William “Vic” Maconachy
Dr. William “Vic” Maconachy
VP for Academic Affairs, Capitol Technology University
wvmaconachy@captechu.edu
In October, 2007, Dr. Maconachy assumed the position of Vice President for Academic Affairs/Chief Academic Officer at Capitol Technology University, Laurel, MD. Dr. Maconachy is charged with sustaining and enhancing the academic quality of programs of study ranging from Business Administration through Engineering, Computer Science and Information Assurance. He also oversees the operations of Distance Learning Services, the Library, The Cyber Battle Lab, and the Space Operations Institute. He is the liaison officer for the university to the Middle States Association. Dr. Maconachy holds the rank of professor, and teaches graduate and undergraduate research courses in Information Assurance.
Prior to Joining Capitol College Dr. Maconachy served at The National Security Agency. While there he held several leadership positions. He was appointed by the Director of the NSA as the Deputy Senior Computer Science Authority where he built a development program for a new generation of Cryptologic Computer Scientists. Prior to this position, Dr. Maconachy served as the Director of the National Information Assurance Education and Training Program (http://www.nsa.gov/ia/academia/acade00001.cfm). He was responsible for implementing a multidimensional, interagency program, providing direct support and guidance to the services, major DoD components, federal agencies, and the greater national Information Infrastructure community. This program fosters the development and implementation of Information Assurance training programs as well as graduate and undergraduate education curricula. In this capacity, he served on several national level government working groups as well as in an advisory capacity to several universities. Dr. Maconachy was the principal architect for several national INFOSEC training standards in the national security systems community. During Dr. Maconachy’s time at the National Security Agency he held many different positions, including work as an Information Assurance Operations Officer, Information Assurance Analyst and a Senior Manager.
Prior to joining the NSA, Dr. Maconachy worked for the Department of Navy. He developed and implemented INFOSEC training programs for users and system maintainers of sophisticated cryptographic equipment. He also served as the Officer In Charge of several INFOSEC-related operations for the Department of Navy, earning him the Dept. of Navy Distinguished Civilian Service medal. Dr. Maconachy holds a Ph.D. from the University of Maryland. He has numerous publications and awards related to Information Assurance, and is the recipient of the prestigious National Cryptologic Meritorious Service Medal. Dr. Maconachy is also the Co-Founder and current Chairman of the Colloquium for Information Systems Security Education (WWW.CISSE.info) CISSE is an international organization of professionals dedicated to advancing Information Assurance Higher Education.
 Professor William Butler
Professor William Butler
Chair Cyber Security, Capitol Technology University
whbutler@captechu.edu
Bill Butler is Chair of the Cyber Security Program at Capitol Technology University. Bill has over twenty years’ experience in the networking and engineering industries as an engineer and consultant. Bill served in the U.S. Marine Corps Reserves and retired as a Colonel. Bill is active in working groups such as the National Institute of Standards and Technology, Cloud Security Alliance, and the National CyberWatch Center. Bill holds degrees from Brenau University, U.S. Army War College, National Defense University, and the University of Maryland. Bill is currently completing his DSc in cyber security at Capitol focusing on preserving cell phone privacy.
 Dr. Helen G. Barker
Dr. Helen G. Barker
Dean of Academics, Capitol Technology University
hgbarker@CapTechU.edu
Dr. Helen Barker serves as Dean of Academics with Capitol Technology University. Before joining Capitol in 2000, Dr. Barker worked in the private sector as a management analyst and resource training specialist in the Washington, DC area and a research analyst in child welfare and economic development in Northern Virginia. Dr. Barker received a B.S.B.A. from Thomas Edison State College, M.S.B.A. from Strayer University, M.S. in Information Telecommunications Management from Capitol Technology University, and doctorate from University of Phoenix in Organizational Leadership. Current research interests include pedagogy relating to online learning and integration of cyber security into business curriculum.