With Phase 1 of the 3GPP 5G Standards mostly finalized as of June 2018, the network equipment vendors can start building the products so that the operators can start commercial deployment of the “official” version of the 5G networks. However, because 5G is much bigger than anyone had anticipated, 3GPP has divided 5G standards in phases so that the network operators can start rolling out their networks for offering 5G services. Phase 2 is due for completion in December of 2019. While Phase 1 of 5G is focused on the use cases that is primarily known as the Enhanced Mobile Broadband, Phases 2 is about Massive Machine Type Communications and Ultra-Reliable and Low-Latency Communications [1].
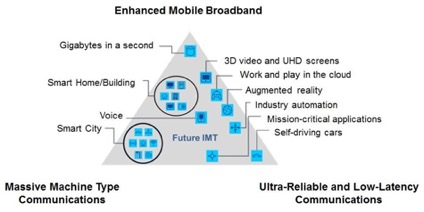
Figure 1. ITU-defined 5G Use Cases
Security, being of the utmost importance for the network operators, is enhanced in Phase 1 of 5G, taking an evolutionary approach with enhancements in a number of areas [2]: cryptographic algorithm enhancements, unified authentication framework, on-demand security policies, and subscriber identity privacy protection. For the most part, the initial 5G network security is identical to that in LTE. Furthermore, additional enhancements will be afforded in Phase 2 to provide the needed security to support Internet of Things (IoT) in both Massive Machine Type Communications and Ultra-Reliable and Low-Latency Communications.
Security aspect of Machine Type Communications, also known as Machine-to-Machine (M2M) and later has become known as what is called IoT today, has long been studied and supported in 3GPP as early as in Release 8 (R8) with various enhancements in later releases. Since the coming of the age of mobile broadband with the release of LTE in R8, the Internet and mobile convergence has taken a giant leap forward, blurring the lines to the oblivion with faster network speeds as well as wider bandwidth. Whether it is called M2M or IoT and whether it is in Release 8 or Release 16, the security goals are the same: to ensure the security of IoT devices and services.
IoT by definition is the network of devices, whether they are embedded in sensors, appliances or automobiles, that enables other things or devices to communicate. These devices are designed to be low cost, low power, and low throughput devices while having communications capabilities such as wired connection using Ethernet or wireless connections using WLAN, Bluetooth, 3G, 4G or 5G technologies. The nature of these devices poses a number of security challenges:
- Physical constraints, low power, low cost, and lack of physical security
- Theft and physical tampering
- DoS/DDoS attacks on the networks
- Unsecure credentials (hardcoded, defaults, etc.), Unsecured interfaces (web interface, open ports), Unsecured configurations
- Unprotected data paths
- Protocol weakness
- SW implementation errors
- Difficult to update firmware, OS, or security patches
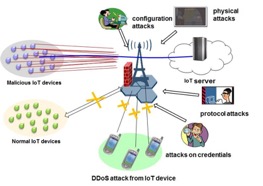
Figure 2. IoT Attacks and Threats
Recent reporting of attacks on the Internet and IoT devices connected to the Internet [3] has been largely attributed to poor security designs that allowed hackers to take advantage of, launching massive and sustained attacks that crippled or slowed down a number of websites including that of Amazon, Netflix, etc. Other attacks that gained notoriety include Stuxnet attack between 2010 and 2014, “Cold in Finland” in 2016,“Mirai botnet” in 2016 and similar “Cold in Finland” attack [4].
To meet the challenges and the requirements, let’s look at some potential security options, including “lightweight” security. Lightweight of course should not be associated with less secure as it would defeat the purpose of the security solution being applied. The goal of lightweight security is not to compromise security by having lower security levels than that of the commonly acceptable (i.e. 128-bit security or equivalent) level or to which the protection level for a particular services is designed for. For example, it would be overkill to design a fool-proof encryption solution for a remote rain sensor that reports whether it is raining or not, a report that consists of one-bit of information with a value of either “1” or “0”. On the other hand, it is not as simple as protecting the trivial and perhaps harmless data being communicated by the sensor, but imagine there are millions of these sensors sending the same report over a wireless network, at best, it causes congestion of the network and at worse, it is a legitimate case of denial-of-service attack. It is rather a design of security that takes into consideration the constraints, use cases of IoT devices, attack vectors, as well as many other aspects. While many security solutions have been incorporated to secure IoT for 4G and earlier, research for IoT security enhancements is still ongoing for 5G. A sample of such options is being explored here. Though these lightweight security considerations alone do not constitute a complete security solution, but are meant to be used in conjunction with other security measures.
Lightweight cryptographic security solutions include design and consideration for cipher algorithm, hash algorithm, authentication algorithm, pseudorandom number generators, and other techniques to live within the constraints of IoT devices. One such algorithm is a block cipher, one that takes a fixed size input and produces a fixed size output (e.g. AES), by a team of researchers from Ruhr-University in Germany, Technical University Denmark in Denmark, and Orange Labs in France [5]. The cipher takes advantage of hardware implementation and achieves comparable security as AES but with much higher efficiencies in terms of power consumption, hardware footprint, code size, and RAM use. Other lightweight cryptographic algorithms [6] are also being researched, studied, and considered for standardizations in ISO/IEC 29192 [7] and possibly other standards such as 5G. These algorithms include block ciphers, stream ciphers, public key algorithms, and message authentication codes, to name a few.
One-time-pad (OTP) is the most secure form of cipher technique there is. Its security lies in the fact that each message being protected with a unique key stream that is used exactly once, making traditional crypto-analysis of plaintext and cipher-text essentially useless. Not traditionally considered as a lightweight security technique, but because of the “single-use and throw-away” nature of the key stream used to protect the message being communicated by IoT devices, OTP is also “light” in the sense that it is a simple XOR operation of the OTP with the OTP. On the downside, OTP needs to be coupled with an efficient or lightweight key stream generator (e.g. hash algorithm) or an efficient key distribution scheme.
Recently, Blockchain technology has gained traction as a security tool for smart contract, among other things. It is used in cryptocurrency, but it is also being considered for IoT. The case of using Blockchain in IoT is also very strong. Not only Blockchain relies on a decentralized architecture that is inherently resilient to single point of failure, it also has mathematically provable immutable and incorruptible characteristics. In IoT security, Blockchain can provide a clean-state proof, an integrity snapshot of the network’s initial state of both the network and the IoT devices that can include software, hardware, firmware, configuration file, security policy, network activities, device location, IP address, user behavior, file system, etc. At run time, it can provide continuous data signature verification to determine whether the network is not compromised, and whether the clean-state proof is still valid. This feature is also particularly helpful for managing and control software for potential attacks on the devices or on the network.
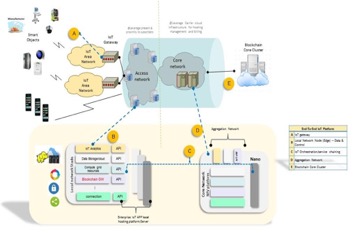
Figure 3. Blockchain and IoT
Many other security solutions are possible, including many network-based solution that emphasize the greater capabilities of the network in securing IoT. In conclusion, this article has only scratched the surface of the potential research and solutions briefly looking into lightweight cryptography, OTP, and Blockchain technology for securing IoT in 5G and beyond. While research in IoT security has come a long way and the resulting technologies are making its way into the standards, much more still needs to be done. There is a fine balancing act as far as IoT security is concerned, taking into consideration IoT devices bound by the limitation of cost, efficiency, power, and security. The constraints are clear and the security goals are clearer. Much more needs to be done to make Internet of Things more ubiquitous and secure than ever. As 5G has just begun, stay tuned.
References:
- ITU-R: “IMT Vision – Framework and overall objectives of future development of IMT for 2020 and beyond”, September, 2015.
- 3GPP TS 33.501: “3rd Generation Partnership Project; Technical Specification Group Services and System Aspect; Security Architecture and procedures for 5G system (R15)”, June, 2018.
- Wall Street Journal: “Hackers Infect Army of Cameras, DVRs for Massive Internet Attack”, September, 2016.
- ZDNet: “Five nightmarish attacks that show the risk of IoT security”, June, 2017.
- Proceedings from Cryptographic Hardware and Embedded Systems – CHES 2007: “PRESENT: An Ultra-Lightweight Block Cipher”, September, 2007.
- Internet Architecture Board Whitepaper: “Lightweight Cryptography for Internet of Things”, March, 2011.
- International Standards Organization: “ISO/IEC 29192 Information technology – Security techniques – Lightweight Cryptography”, January, 2015.
Marcus Wong  has over 20 years of experience in the wireless network security field with AT&T Bell Laboratories, AT&T Laboratories, Lucent Technologies, and Samsung’s Advanced Institute of Technology. He is certified CISSP.
has over 20 years of experience in the wireless network security field with AT&T Bell Laboratories, AT&T Laboratories, Lucent Technologies, and Samsung’s Advanced Institute of Technology. He is certified CISSP.
Marcus has concentrated his research and work in many aspects of security in wireless communication systems. Marcus joined Huawei Technologies (USA) in 2007 and continued his focus on research and standardization. Marcus has held elected official positions in both WWRF and 3GPP. He also served as guest editor in the IEEE Vehicular Technology magazine. As an active contributor, author, and publisher, he has shared his security research on a variety of whitepapers, book chapters, and speaking engagements.
