Protecting first responder and local user data is of critical importance, especially if data contains Personal Identifiable Information, or PII. The majority of humanitarian networks utilize ad hoc configurations in a disaster zone. When ad hoc networks are installed, little thought is given to the variety of cyber threats that are out in the field, ranging from malicious applications to denial of service. Technological advances in security features are constantly improving the cybersecurity landscape to include:
- Improved processing performance
- Rapid threat intelligence and remediation
- Portability of hardware
- Simplified security configuration management.
These advanced security features have been deployed in past disaster responses and can easily be implemented by today’s disaster response teams in their communications solutions. Humanitarian cybersecurity practices must constantly evolve to protect against opportunistic threats. These practices must also be open to innovation that can detect and mitigate threats in real time with little human intervention, and ultimately eliminating these threats by early detection of damaging intent.
Online connectivity during normal day-to-day life is important. We do ordinary tasks such as checking emails, checking the weather and traffic, and using social media to see what friends and family are doing. Additionally, we also use internet connectivity check more sensitive information such as our bank accounts, pay bills online, and transfer money. A natural disaster significantly disrupts our online life. Imagine a Category 4 or 5 hurricane ripping through a local area destroying infrastructure. When this happens, connectivity disappears in an instant, on top of electricity and water becoming unavailable, and homes damaged or destroyed. Of course in those critical moments, the humanitarian response efforts will focus on rescues and maintaining life. Communications play vital, high-level roles in synchronizing these efforts during a disaster response:
- Relay assessment information on affected areas
- Coordination medium for first responders
- Providing a means of communication for affected population
The scarcity of communications and energy resource in the aftermath of a disaster makes for constructing a robust, redundant, and highly secure network particularly challenging. Often the default mindset of relief workers trying to aid in IT connectivity, is to establish ad hoc data and voice networks as fast as possible. While any type of service that can be made available for communications is more desirable than no service at all, this should not preclude incorporating network security measures in the communications solution to protect the network clients.
For example, a municipal Emergency Operations Center (EOC) needs to report its status to the Regional Coordinating Center. When communication kits are installed to fulfill this purpose, there are key considerations during the setup and implementation of service availability. These include the operational responsibility of protecting data, its integrity, and availability, especially if it contains PII, or critical mapping and location information necessary for the continued operation of the EOC.
Further complicating service availability are highly latent and very expensive satellite uplinks that must be protected from unauthorized intrusion or worse, a denial of service attack. Limited bandwidth from satellite links also requires prioritization of data traffic types on the network as a standard practice, to allow important services such as Voice over IP unabated access. Content filtering of non-critical internet traffic categories may be necessary to prevent network congestion that could result in severe degradation of accessibility and quality of service.
This paper will discuss the two concepts that all disaster relief agencies must consider when setting up their communication networks in disaster areas:
- INTEGRATING SECURITY
- REAL-WORLD DEPLOYMENT
According to an Office for the Coordination of Humanitarian Affairs (OCHA) policy paper Humanitarianism in the Age of Cyber-Warfare, humanitarian organizations need to recognize information security as a fundamental aspect of operations. These organizations need to work more closely with data security experts when setting up networks and other tools, and ensure regular reviews of vulnerabilities and breaches [1]. Security must be incorporated at multiple levels within the network. This ‘defense-in-depth’ approach offers layers of security for a multitude of threat vectors, beginning with end user devices. Smartphones, tablets, and laptops are assumed to be vulnerable if updates or patches are not installed. Risky user activity and phishing can also compromise not only the user device but other devices on the local area network. Modern networking tools allow for a generalized assessment of potential threats to vulnerable devices, and corresponding Advanced Malware Protection systems from security appliances can mitigate the threat until security updates are applied.
By carefully integrating security features into your network configurations before disasters happen, these functionalities become available for rapid deployment into the disaster zone and scalable to support an increasing number of users.
It is impractical to assume all users of the disaster networks are technically proficient in advanced security practices. Engineers designing and configuring these disaster response solutions must consider the evolving threats during analysis, and include advance security throughout the design of communications solution. Management of security controls should be simplified and self-evident on a streamlined user interface.
During the Hurricane Maria disaster response, a site in Puerto Rico served by NetHope’s emergency network had numerous queries to compromised DNS servers, malicious browser plugin activities, and malware being blocked by a Meraki MX (Figure 1). These security events happened during users’ normal online activity, perhaps running in the host’s background, and sometimes without any obvious signs of security threats or malicious activity from programs and applications.
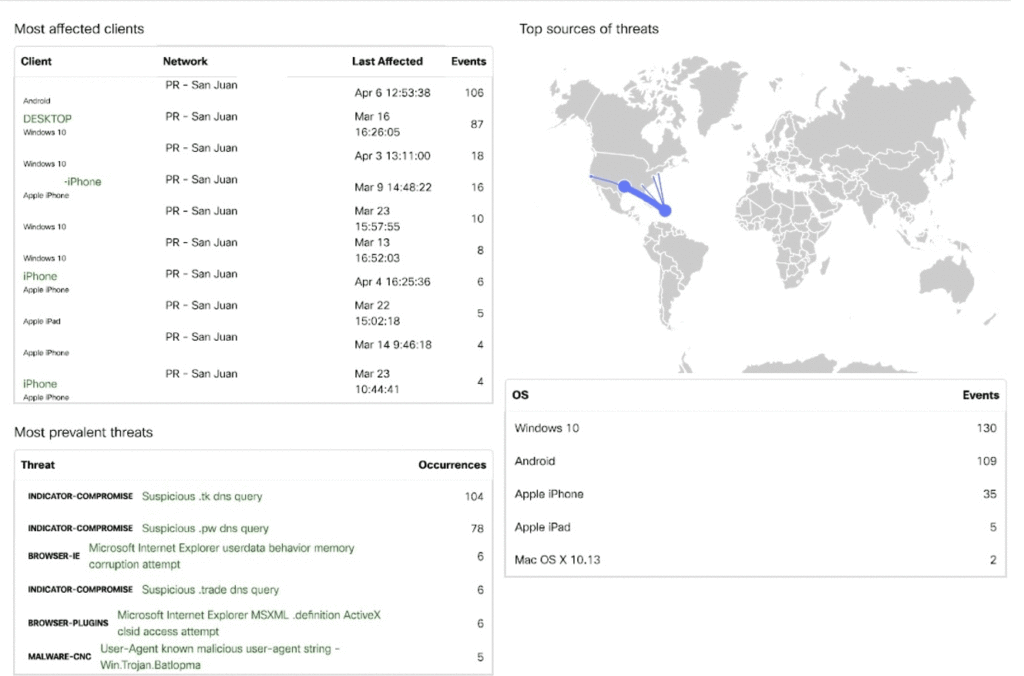 Figure 1. Meraki dashboard security report on emergency network supporting a site in Puerto Rico
Figure 1. Meraki dashboard security report on emergency network supporting a site in Puerto Rico
Disaster response teams such as Cisco Tactical Operations (TacOps) utilize compact, easily configurable, and highly secure Meraki MX security appliances in field deployments as recently as the Hurricane Maria response in Puerto Rico. The Meraki MX security appliance is at the heart of almost every network deployed across the island. Not only does it perform the basic routing and switching but more importantly, it protects the communication path. Meraki implemented and maintains a security program that leverages the ISO/IEC 2700 series of control standards as its baseline [2].
The dynamic situations at disaster sites typically result in significant and continuous changes in communication requirements. In most disasters, by the time the humanitarian response teams arrive for network installation, the service needs will most likely be different than what was requested initially. Disaster response teams, as well as the equipment used in establishing connectivity, need to be flexible and adapt to the reconfiguration needed, while also meeting the changing requirements in a secure manner. Within all the modifications, conforming security measures need to be mindful of the type of data transmitted and received, in order to properly separate and prioritize critical and non-critical information, software, and applications. The same level of data protection built in the original network design should be afforded to any redesign done in the field.
We are in an era where advanced security is becoming more intelligent, faster, less complex to configure, and less resource intensive. All of these characteristics are enabling quicker deployment in locations closer to the affected population.
Industry disaster response groups and all humanitarian networks must incorporate updated security to protect the integrity, privacy and confidentiality, and availability of information. The pace of technological advancement means that engineers have more tools available to design innovative security practices. Ultimately all the innovation, implementation, research and development are geared towards protecting critical first responder and user data.
 Ron Snyder is a Solutions Architect for Cisco Tactical Operations, a dedicated crisis response team that establishes emergency networks in the aftermath of a disaster. A member of TacOps since May 2013, he is responsible for leading the strategy and technical direction of the team’s network infrastructure and deployable communications solutions. Ron also deploys and supports mobile communications platforms such as the Network Emergency Response Vehicle, a.k.a. the NERV, Mobile Command Vehicle, and smaller kits such as the Mesh Response Kits and Emergency Communications Kits. He has deployed to provide communications support in disasters such as the 2017 Hurricane Maria response in Puerto Rico, 2016 Ecuador earthquake, European Refugee Crisis in Slovenia, Cyclone Pam in Vanuatu, and Super Typhoon Haiyan in the Philippines.
Ron previously worked at the Camp Roberts SATCOM facility in Paso Robles, creating the Standard Operating Procedures and training program for Regional Hub Node operators serving the US Army.
Ron Snyder is a Solutions Architect for Cisco Tactical Operations, a dedicated crisis response team that establishes emergency networks in the aftermath of a disaster. A member of TacOps since May 2013, he is responsible for leading the strategy and technical direction of the team’s network infrastructure and deployable communications solutions. Ron also deploys and supports mobile communications platforms such as the Network Emergency Response Vehicle, a.k.a. the NERV, Mobile Command Vehicle, and smaller kits such as the Mesh Response Kits and Emergency Communications Kits. He has deployed to provide communications support in disasters such as the 2017 Hurricane Maria response in Puerto Rico, 2016 Ecuador earthquake, European Refugee Crisis in Slovenia, Cyclone Pam in Vanuatu, and Super Typhoon Haiyan in the Philippines.
Ron previously worked at the Camp Roberts SATCOM facility in Paso Robles, creating the Standard Operating Procedures and training program for Regional Hub Node operators serving the US Army.
